All you need to know about AWS IAM - Part 1
AWS Identity and Access Management services securely manages identities and access to AWS services and resources. To understand how, read on!!
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. With IAM, you can centrally manage permissions that control which AWS resources users can access. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
Specific Targets for IAM :
Set and manage guardrails and fine-grained access controls for your workforce and workloads
Manage identities across single AWS accounts or centrally connect identities to multiple AWS accounts.
Grant temporary security credentials for workloads that access your AWS resources.
Continually analyze access to right-size permissions on the journey to least privilege.
How IAM works?
With AWS Identity and Access Management (IAM), one can specify who or what can access services and resources in AWS, centrally manage fine-grained permissions, and analyze access to refine permissions across AWS.
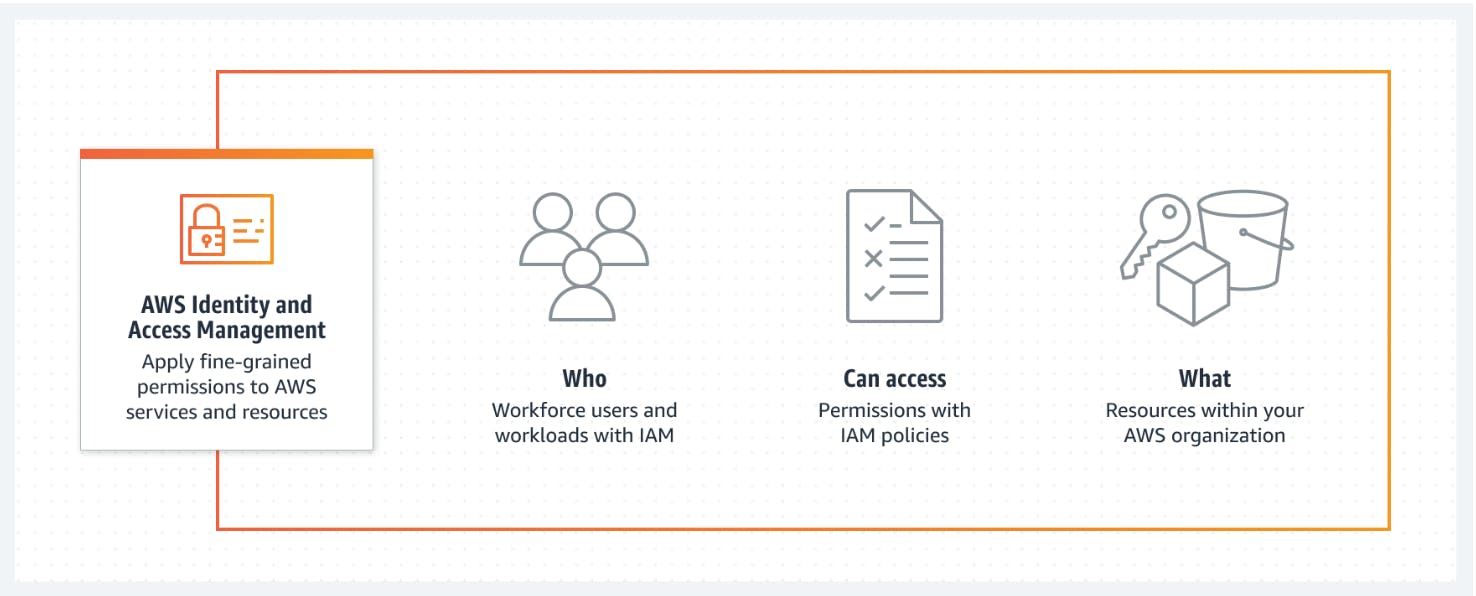
Why use IAM?
AWS customers can use IAM to manage and scale workload and workforce access securely supporting their agility and innovation through AWS.
Use Cases :
1) Apply fine-grained permissions and scale with attribute-based access control
So, what exactly do you mean by attribute-based access control?
Attribute-based access control (ABAC) is an authorization strategy that lets you create fine-grained permissions based on user attributes, such as department, job role, and team name. User attributes make permissions more intuitive, and they simplify the administrative experience of managing access. By specifying permissions using attributes, you can reduce the number of distinct permissions that you need for creating fine-grained controls in your AWS account.
For example, instead of creating AWS Identity and Access Management (IAM) roles with distinct policies for every team or individual to ensure the right levels of access, you can use ABAC to group attributes to identify which resources a set of users can access. Then, as you add new users and resources, you can associate the appropriate attributes so that the right users have access to the right resources. It’s no longer necessary to update existing policies to allow new users to access resources. With attribute-based access controls, your authorization strategy can scale at the pace of your innovation.
Hop in to learn about the services you can use in your ABAC strategy.
One important point is to ensure that permissions are granted based on IAM attributes when accessing shared resources. When you base permissions on attributes, you can control the level of access a user has to shared AWS resources. For example, by using the same IAM role, you can grant one developer, John, read-only access to an AWS Secrets Manager secret owned by another developer, Saanvi, on his same team because John’s team attribute is equal to the team tag on Saanvi’s secret. This is possible because their IAM role’s permissions are based on a team name attribute. The secret instance may be tagged as created by Saanvi, so she is granted full access to the secret.
Because entitlements are based on the human user’s attributes and not their role’s permissions, John and Saanvi might be granted the same level of access to that secret across different roles.
Here are some related links you might want to check-in:
ABAC versus RBAC (Role-based Access Control)-https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction_attribute-based-access-control.html#introduction_attribute-based-access-control_compare-rbac
Configure ABAC in AWS by using AWS IAM-https://docs.aws.amazon.com/singlesignon/latest/userguide/abac-checklist.html
Use ABAC with Amazon Cognito identity pools-https://docs.aws.amazon.com/cognito/latest/developerguide/attributes-for-access-control.html
2) Manage per-account access or scale access across AWS accounts and applications
Manage per-account identities with IAM or use IAM Identity Center to provide multi-account access and application assignments across AWS.
How IAM Identity Center works-
AWS IAM Identity Center (successor to AWS Single Sign-On) helps you securely create or connect your workforce identities and manage their access centrally across AWS accounts and applications. IAM Identity Center is the recommended approach for workforce authentication and authorization on AWS for organizations of any size and type.
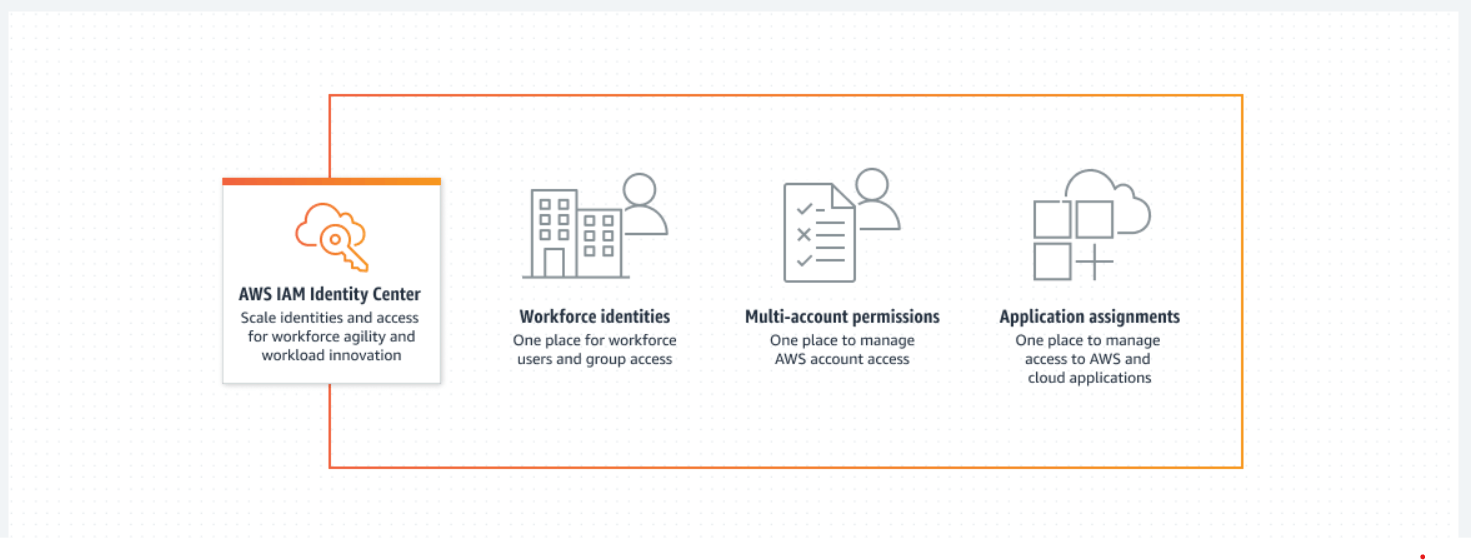
Use Cases :
Enable multi-account access to your AWS accounts-
Your users can use their directory credentials for single sign-on access to multiple AWS accounts. Their personalized web user portal shows their assigned roles in AWS accounts in one place. Users can also single sign-on through the AWS Command Line Interface (CLI), AWS SDKs, or AWS Console Mobile Application using their directory credentials for a consistent authentication experience.
Enable single sign-on access to your AWS applications-
IAM Identity Center is integrated with applications such as Amazon SageMaker Studio, AWS Systems Manager Change Manager, and AWS IoT SiteWise for zero-configuration authentication and authorization. These integrated applications share a consistent view of users and groups for resource sharing and collaboration all within the application.
Enable single sign-on access to Amazon EC2 Windows instances-
Securely access your Amazon EC2 Windows instances with existing corporate user names, passwords, and MFA devices. You are not required to share administrator credentials, access credentials multiple times, or configure remote access client software. You can centrally grant and revoke access to your EC2 Windows instances at scale across multiple AWS accounts.
Enable single sign-on access to cloud-based applications-
You can more easily configure single sign-on access to applications that support SAML 2.0 using the IAM Identity Center application configuration wizard. IAM Identity Center also provides preconfigured settings for many cloud applications, including Salesforce, Box, and Microsoft 365.
Alright, seems like it's getting longer for a single blog! See you at the next one where we'll see how AWS helps Establish organization-wide and preventative guardrails! Happy Learning!!

